|
|
Web Hosting by Netfirms | Free Domain Names by Netfirms |
|
IPsec parameters used in this example are mentioned below.
Encryption – AES128
Hashing – SHA
Diffie Helman Group – 2
Perfect Forward Secrecy (PFS) – On
Remote Subnet – 1.2.3.0/24
Host at head end – 172.28.237.243/32
Preshared key – 123456 (This is only for testing purposes)
1. A tunnel interface will be created from Network à Interfaces menu
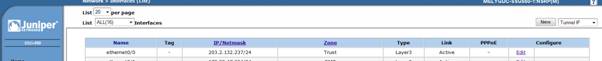
2. Tunnel interface would be configured to be bound to the internet interface (Eth0/2) and Internet zone.
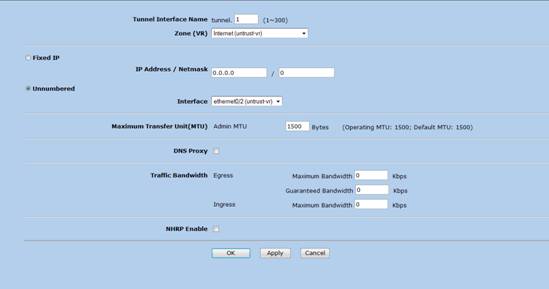
3. From VPNàAutokey Advanced à Gateway menu create a Phase 1 policy as follows. Things to note in this step are
Remote Gateway IP address – Need to find out from the remote party
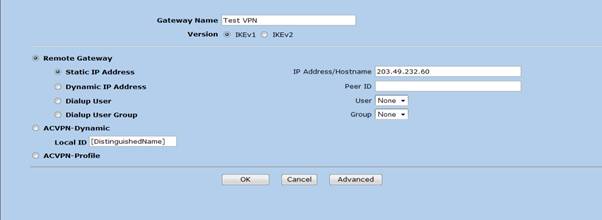
4. Upon completing the above by pressing the “Advanced” button would take to the following screen. Things to note here are
Preshared Key – Must be communicated with the remote party before the configuration
Outgoing interface – Interface where the firewall connects to the internet (Ethernet 0/2)
Phase 1 proposal – Must be equivalent with the remote peer
The other settings can be left as default. Once completed click on Return and Ok to finish Phase 1 configuration

5. To configure Phase 2 setting move to VPN à Autokey IKE menu and click “NEW”. Screen similar to the following would appear the things which needs to be specified are
Remote gateway – Select the Phase 1 proposal created in the previous step
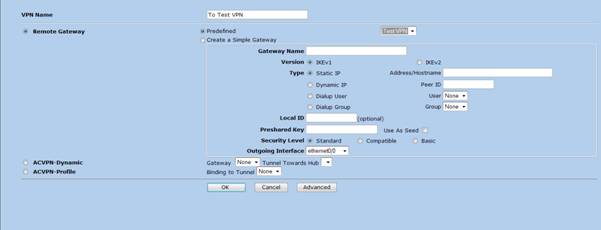
6. By clicking the “Advanced” button screen similar to the following would appear. Following items needs to be specified and the rest can be left with the default values
Phase 2 Proposal – Select the proposal which was communicated with the remote party
Tunnel Interface – Specify the tunnel interface which was created in step 1 & 2.
When completed click on the “Return” button and the “Ok” button to completed Phase 2 configuration
Note – When peering non Juniper devices Proxy ID’s must be specified. Proxy ID must match the remote end access list which defines the interesting traffic allowed to traverse through the tunnel. For example if the local subnet is 172.28.0.0/16 and remote subnet is 1.2.3.0/24 these should be specified in Local IP and Remote IP text boxes respectively.
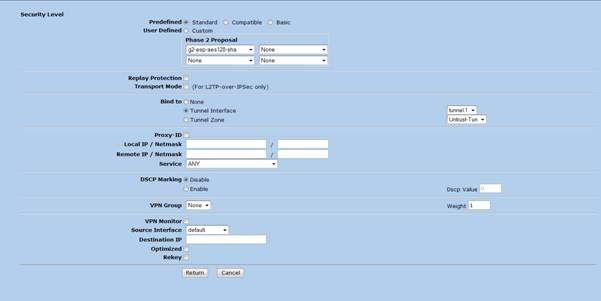
7. Once IPSec related configurations are completed a route must be configured as follows to the remote subnet pointing to the tunnel interface from Network à Routing à Destination menu.
Note – Gateway IP will not be specified for subnets traversing across VPN tunnels
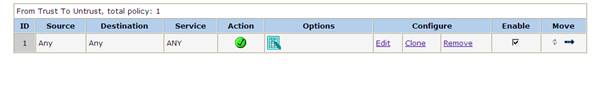
8. Necessary firewall rules must be created to and from the zones to permit traffic. Following is a generic rule added for testing purposes from Trust à Internet Zone.
![]()
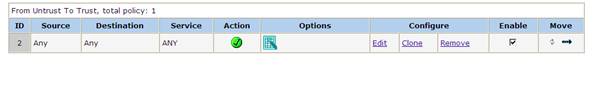
A rule as follows can be created from Internet à Trust zone if any traffic will be originated from the remote subnet
![]()
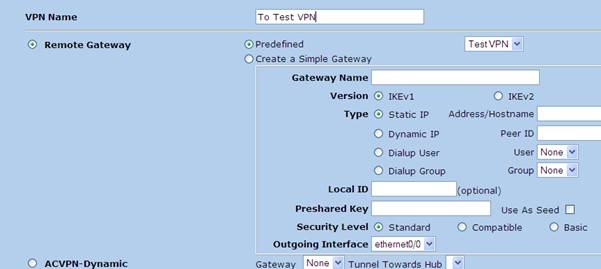
The steps would be similar to the head end configuration but some values in the configuration would be reversed. Following will describe the configuration steps need to peer with the SSG550 configured above. To be compatible with the head end configuration following IPsec parameters were used
Encryption – AES128
Hashing – SHA
Diffie Helman Group – 2
Perfect Forward Secrecy (PFS) – On
Remote Subnet – 1.2.3.0/24
Host at head end – 172.28.237.243/32
Preshared key – 123456
1. Tunnel interface creation

2. Phase 1 Configuration
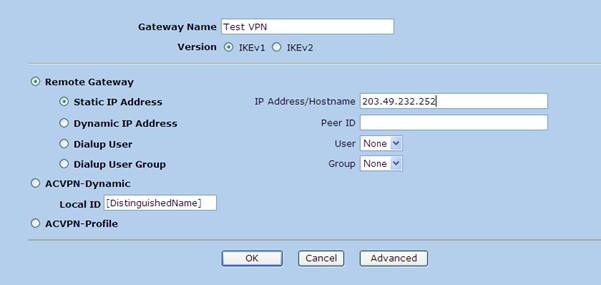
Note – Peer IP should be the NSRP IP of the SSG 550 which is 203.49.232.252
3. Phase 1 Advanced configuration
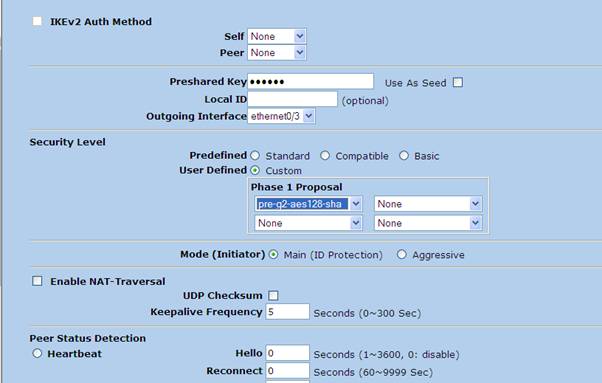
4. Phase 2 Configuration
5. Phase 2 Advanced configuration
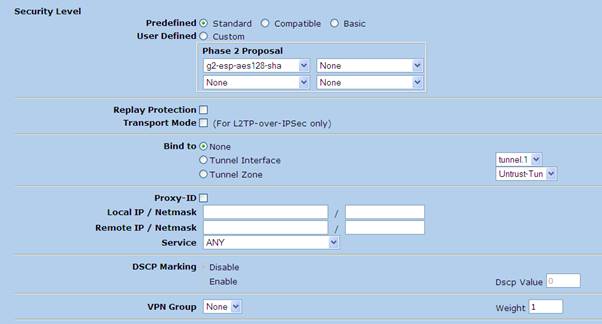
Note – The tunnel interface created in Step 1 must be bound to Phase 2 from this screen
6. Route configuration
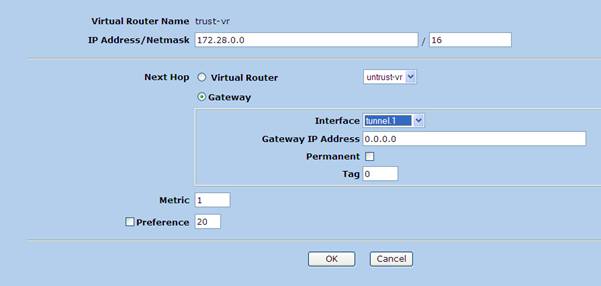
7. Firewall rules created to and from the zones. (The rules used in this example are very much relaxed but source destination IP restricted rules must be used in production)
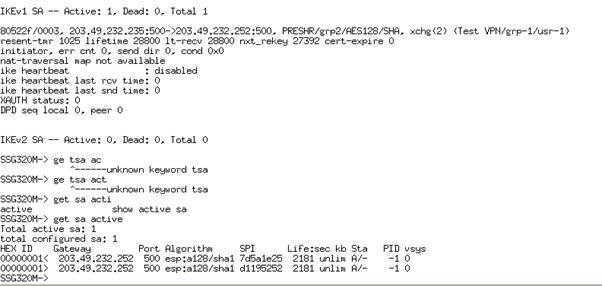
Once the above steps are completed originate some traffic from the either end as firewall rules permit and check the status of the tunnel from the devices using the following commands
Get ike cookies – lists the successful completion of phase 1
Get sa active – list the successful completion of phase 2
Below screen shot is a sample output of the above commands after a successful completion of phase 1 & 2.
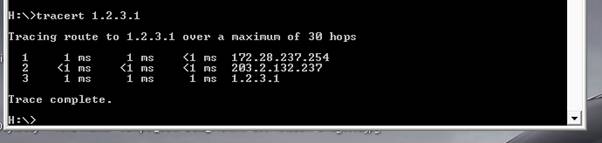
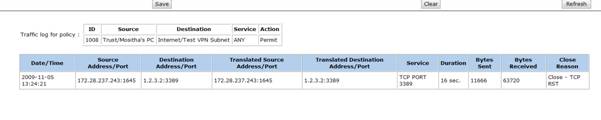
8. Further verification can be done by using PING and TRACERT if firewalls rules permits and by checking the traffic logs of the rules
The following CISCO configuration uses the existing Phase 1 and Phase 2 parameters used in above steps to peer with the SSG 550.
1. Phase 1 configuration
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key 123456 address 203.49.232.252 255.255.255.0 no-xauth
2. Configure an access list to define traffic which needs to be encrypted through the tunnel
access-list 101 permit ip 1.2.3.0 0.0.0.255 172.28.0.0 0.0.255.255
Note – On the Juniper end the exact subnets used in the above access list must be specified under “Proxy ID” section in VPN à Auto Key IKE VPN policy’s advanced settings
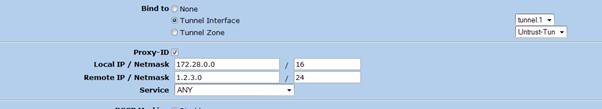
3. Phase 2 configuration
crypto ipsec transform-set AES128-SHA esp-aes esp-sha-hmac
crypto map TEST_VPN 10 ipsec-isakmp
set peer 203.49.232.252
set transform-set AES128-SHA
set pfs group2
match address 101
4. Attach the crypto map to the outgoing interface as follows
interface GigabitEthernet0/1
ip address 203.49.232.235 255.255.255.0
duplex auto
speed auto
crypto map TEST_VPN
5. Add a static route to the head end traffic
ip route 172.28.237.243 255.255.255.255 203.49.232.252
6. To test phase 1 use show crypto isakmp sa command the output should be similar to the following if the tunnel has negotiated correctly
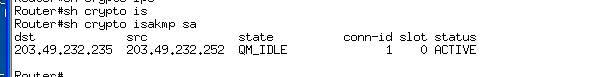
7. Phase 2 can be tested using show crypto ipsec sa command and the output should be similar to the following
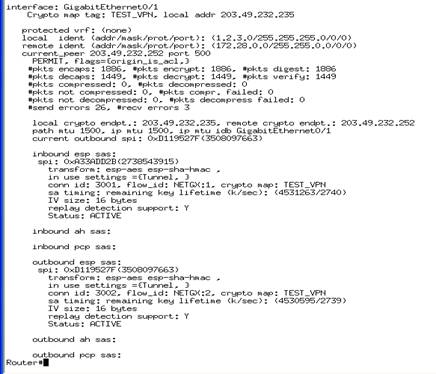
8. Further testing can be done using PING and TRACERT commands as follows